how to hack using Webdav
webdav hacking tutorial is one of the simplest method of hacking, it somehow easy to understant, lemme cut the story short, kindly follow my precedure patiently
first ofAll download webdav software
HERE
To search for vulnerable web use this webdav
following dorkz below:
inurl: Hmei7.asp; .txt
inurl: Umer.asp; .txt
intitle: "index.of" intext: "(Win32)
intitle: "index.of" intext: "(Win32)
intitle: "index.of" intext: "(Win32)
DAV / 2?
inurl: webdav
inurl: .com.ng / *. asp
inurl: .com / *. asp
inurl: .net / *. asp
copy one dork above. Now go
to www.google.com and paste dork into the search box as shown
below.

Now open webdav tool. Do not forget to
turn off antivirus before opening
webdav. This is a view webdav. How cool
is that, there is a picture of Patrick lol.

Firstly click WebDav on the menu bar, then click Asp shell maker

Wait until a new window appears as below, then click the Settings menu.

Later appeared the form to set the file name and the script as below, click Load from file Shell..

Now locate the script deface agan already prepared. The file may be in the form of .html or .txt file, then click open.

See i've changed the script. Now edit the file name on the menu Name of your shell. Here I love the example name isc.html and if already changed, press the button Hide me.
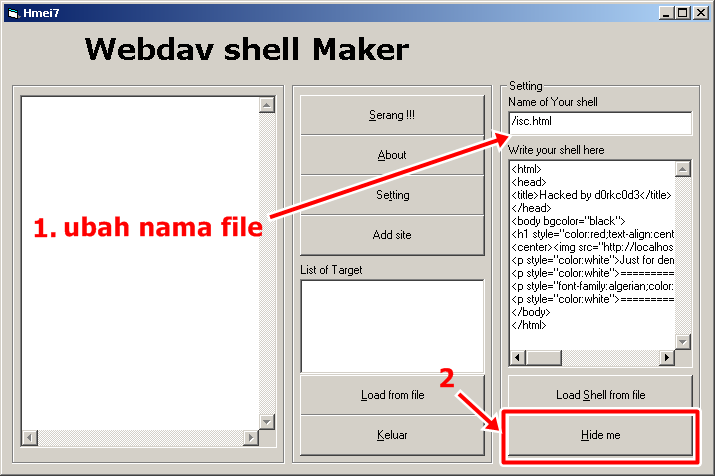
Well weapons already ready to be used now enter the target. Xixixi, already rich want to combat wrote: The target is filled according to search results on google dork earlier. I click the
button Add Site.

Enter the url of the target and then click OK.

Now click Attack !!!

Click OK.

Later, if successful, it will be written as shown below.

Copy the url above http://www.e-ctasia.com/isc.html then paste in the address bar and hit enter...
If not succeed, try again and look for another target. You're done, Hopefully the tutorial is easy to understand :)

















